In 2025, how should IT companies construct a secure local area network?
Hi there, network administrators and techies! In 2025, the cybersecurity industry has changed to resemble a high-stakes version of “Where’s Waldo?” but with hackers in place of the elusive figure wearing the red and white striped hat. Corenet groups CEO Ashley say: Safety comes first and foremost.
Step 1: The Basis: Infrastructure and Planning
You need a good strategy before you even consider setting up routers or putting in connections. If you were constructing a home, you wouldn’t begin with the roof, would you? Your LAN is no different.
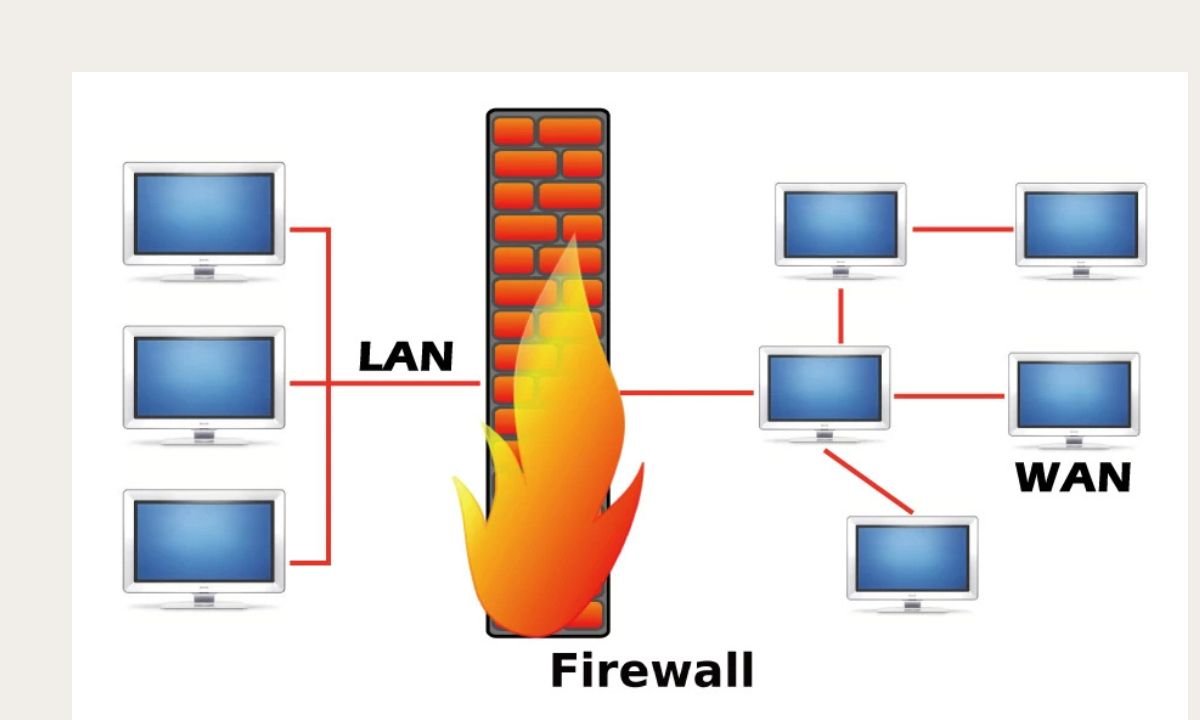
Step 2: Your First Line of Defense: The Firewall
It can be like to playing a high-stakes game of chess to configure your firewall. You must create rules that only let required traffic to pass through while preventing all other traffic. Be precise and avoid leaving any openings for hackers to take advantage of. Read those setup guides as carefully as you would a best-selling book because, as they say, the minutiae are crucial.
Step 3: Encryption: The Technique of Making Information Unintelligible
It is not possible to “set it and forget it” with encryption. Make sure your encryption settings are still up to date by auditing them on a regular basis. Consider it similar to checking your car’s oil: you wouldn’t want to be stuck with your engine blown, would you?
Step 4: Access Control: Your Network’s Gatekeeper
Depending on their work duties, provide access to your staff. For instance, the IT team does not require access to critical customer data, and the HR department does not require access to the financial system. Your network will remain more secure if you follow the least privilege concept. Consider it like assigning duties to your children: you wouldn’t give them the car keys only because they politely requested, would you?
Step 5: Monitoring and Logging: Your Network’s Eyes and Ears
Logging and monitoring are similar to installing security cameras in your workplace. It monitors everything and logs any questionable activities.

If you’re a tech company tasked with setting up a secure Local Area Network (LAN), you’re in for quite a ride filled with firewalls, encryption, and perhaps, a dash of humor to keep our sanity intact. Buckle up, because we’re diving into a world where security isn’t just a buzzword—it’s a way of life.